
Don’t fall for SMISHING

STOP! Don’t respond to that urgent text telling you to do something. It could be a SMISHING hack.
Review your cybersecurity practices. Hackers are busy around elections.
Hackers use phishing to compromise systems and networks and trick people into acting on bad information. This can lead to unauthorized access to an election network, official social media accounts or email accounts. Hacks can disruption the election process. Messages may be mistakenly distributed with errors, causing recipients to carry out misguided action, such as attempting to vote on the wrong day or location. These scenarios may lead to a decline in public confidence in the election process. – CISA
Phishing is a cybercrime in which a target is contacted by someone posing as a legitimate institution to trick them into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. Phishing by text message is SMISHING.
Social engineering uses psychological manipulation to trick people into divulging confidential information. This great KnowBe4 resource explains 22 social engineering red flags to be on the look out for.
Watch for these signs of a hacker
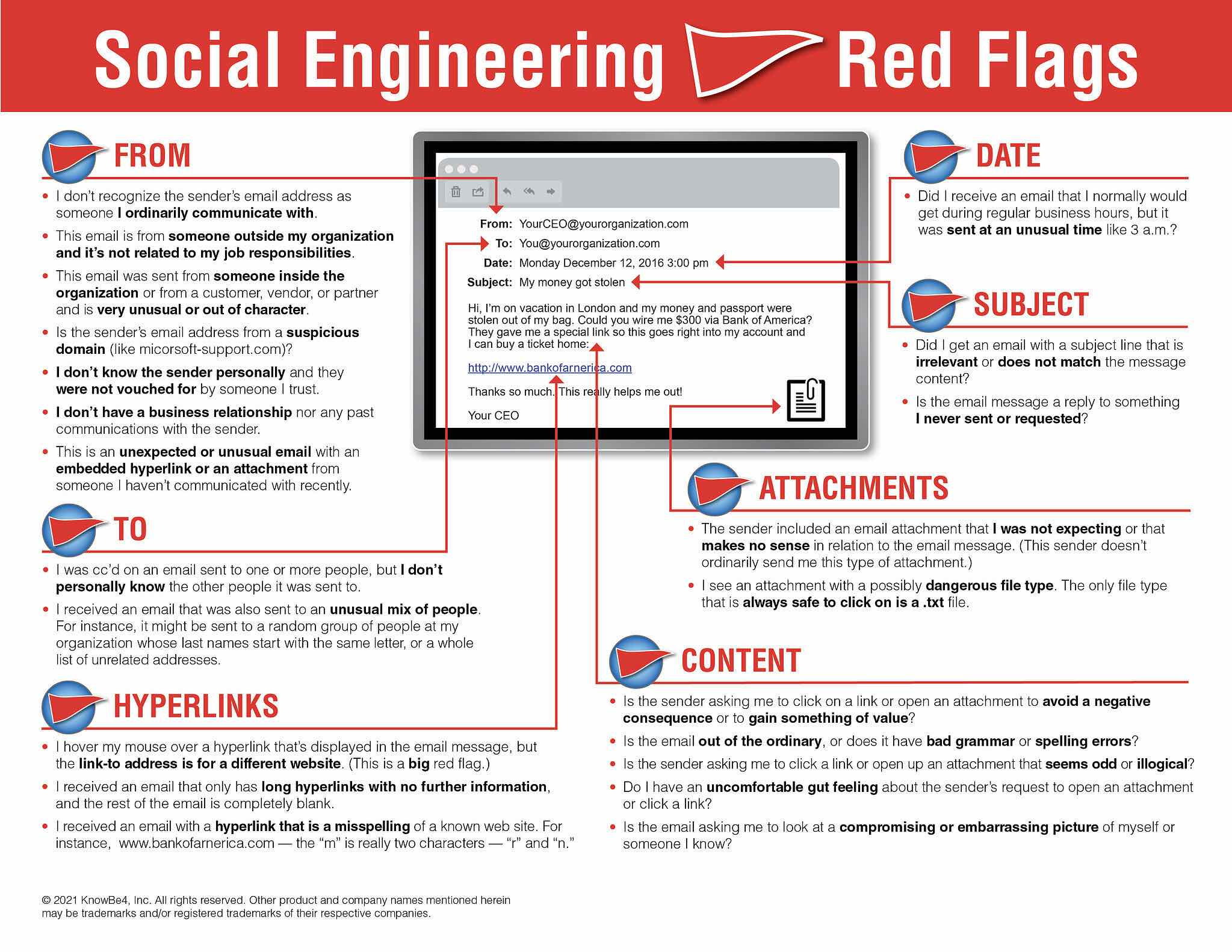
SMISHING
Smishing messages convey a sense of urgency to socially engineer the victim into responding without fully evaluating the request. The most common smishing scams relate to user credentials for businesses or financial institutions, gift offers, invoices, package delivery confirmations, and overdue payments. Text messages can contain links to such things as webpages, email addresses or phone numbers that when clicked may automatically open a browser window or email message or dial a number. This increases the likelihood that users will fall victim to engineered malicious activity. – CI Security
Would you fall for these hacks?
You have a package. Check on its delivery status. Some delivery companies use SMS to update their consumers, but they use links directing to their domains. Scams typically use URL shorteners or have domain names that try to approximate a legit one.

You’ve won! f you did enter a contest recently, these messages can easily lead to malware on your device if you have entered a contest recently. Remember that most legitimate contest wins are communicated over email.

Change your password. A warning that alerts you that have been hacked and need to change your password immediately. And you may be directed to a malicious website to create a new password.

Your credit has been hacked. Call this hotline to confirm your identity and get a new credit card.

I need help. A relative or friend has lost their wallet and passport – and they need your help. They would like you to send them emergency funds.

The boss need this your help. Your boss is traveling / on vacation and cannot access some key information. He’s asked you to text it to him directly right away.

There has been a security hack. Please reset all passwords and standby for instructions from an emergency security team that has been set up. (Don’t worry about their Russian accents).

This is urgent. You have to move fast and immediately click on a special link to get an emergency patch to update voting machines. Learn more at TerraNova Security
What is a social engineering attack?
In a social engineering attack, an attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems. An attacker may seem unassuming and respectable, possibly claiming to be a new employee, repair person, or researcher and even offering credentials to support that identity. However, by asking questions, he or she may be able to piece together enough information to infiltrate an organization’s network. If an attacker is not able to gather enough information from one source, he or she may contact another source within the same organization and rely on the information from the first source to add to his or her credibility. CISA
Cybersecurity and Infrastructure Security Agency
The Cybersecurity and Infrastructure Security Agency (CISA) leads the national effort to reduce risk to our cyber and physical infrastructure. It connects people to resources, analyses, and tools to help them build their own cyber, communications, and physical security and resilience, in turn helping to ensure a secure and resilient infrastructure for the American people.
More cybersecurity resources
- Protect your online privacy as Republicans unleash bounty hunters in their war on women.
- Project Veritas agent? Check their identity with free Google facial recognition.
- Guard against hackers. Reduce your digital footprint.
- Don’t be conned! Ten safety tips against political sting operations.
- Three Free Safety Apps For Protestors
- How Small Adversaries Overwhelm Superpowers With Cyber Warfare And Disinformation
- Beware Of Free Gifts. How Hackers Use Social Media To Profile And Trick Their Victims.
TakeAway: Be on guard against hackers and SMISHING.
Deepak
DemLabs
DISCLAIMER: ALTHOUGH THE DATA FOUND IN THIS BLOG AND INFOGRAPHIC HAS BEEN PRODUCED AND PROCESSED FROM SOURCES BELIEVED TO BE RELIABLE, NO WARRANTY EXPRESSED OR IMPLIED CAN BE MADE REGARDING THE ACCURACY, COMPLETENESS, LEGALITY OR RELIABILITY OF ANY SUCH INFORMATION. THIS DISCLAIMER APPLIES TO ANY USES OF THE INFORMATION WHETHER ISOLATED OR AGGREGATE USES THEREOF.
Read in browser »
Reposted from Democracy Labs with permission.












